SharePoint Online DMS Configuration
It is highly recommended to proceed through this entire article for best results with setting up a Sharepoint integration.
For users that would prefer a PDF version of this section, please click the PDF icon in the upper right corner of this page.
Prerequisites
The following list includes the software and files needed to follow this walk-through and authorize communication between TeamConnect and SharePoint Online:
- An Office 365 subscription plan that includes:
- SharePoint Online
- Azure Active Directory
- (Examples of such plans include: Office 365 Business Essentials, Office 365 Business, and Office 365 Business Premium)
- JDK 8
- The latest version of the following files:
SharePointOnlineIntegration.classSharePointOnlineIntegration.properties
The Baltimore CyberTrust Root certificate installed in your application server's trust store.
- A PEM encoded X.509 public certificate
- This certificate must be a PEM (Base-64) encoded X.509 public certificate, which will typically have either the .CER, .CRT, or .PEM file extension; if you are in a development environment or did not acquire such a certificate through your certificate authority of choice, you may create a self-signed one using the key length of your choice (4096 bits is recommended).
- A PEM encoded PKCS #8 private key complementary to the X.509 public certificate
- This private key must be a PEM (Base-64) encoded PKCS #8 private key, which will typically have the .PK8 file extension; if you are in a development environment or did not acquire such a file through your certificate authority of choice, you may create one.
-
Note: Due to the sensitive value it contains, if this file has been supplied for the sole purpose of authorizing TeamConnect to communicate with SharePoint Online, it is strongly recommended after setting up your integration(s) that you move this file to a secure location or remove it from your system entirely; once this value is given to TeamConnect through the DMS Connector page, it will be obfuscated in the user interface upon entry and encrypted within the database for secure storage.
(Optional) Creating a self-signed X.509 public certificate and PKCS #8 file on Windows 7
As this scheme requires the uses of public certificates, the following software may be used to create a self-signed certificate and private key file using the Microsoft Windows 7 SDK:
- Latest version of Microsoft .NET Framework 4
- Microsoft Windows SDK for Windows 7 and .NET Framework 4
- Latest version of OpenSSL for Windows
More information on setting up self-signed public certificates can be found in the Self-Signed Public Certificates for DMS section.
SharePoint OAuth Setup
The following section needs to be read and completed prior to progressing with DMS Connector setup.
When using a web application to make RESTful API calls against SharePoint Online, there is an initial set up required to establish a level of trust between your application, SharePoint Online, and the authorization server that SharePoint Online trusts (Azure Active Directory). This article provides a walk-through on how to establish this trust using the OAuth 2.0 client credentials flow. Using this scheme allows a client application to function similar to a background service, in that it can make web service calls on behalf of users without requiring their active participation.
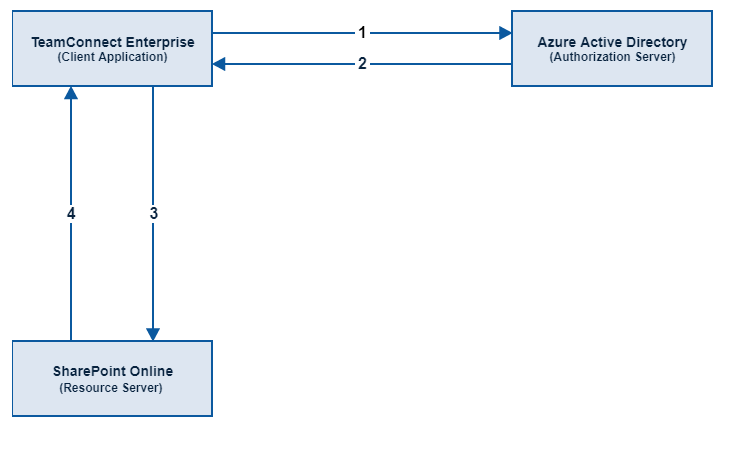
Using Azure AD, TeamConnect Enterprise, and SharePoint Online as an example:
- Using a shared secret, TeamConnect requests an access token from Azure AD by making a call to the endpoint: https://login.microsoftonline.com/common/oauth2/token
- TeamConnect receives a response containing an access token from Azure AD
- TeamConnect uses the access token to request document library information from SharePoint Online
- TeamConnect receives a response containing information about the document library
Self-Signed Public Certificates for DMS
Users must ensure that the following software has been installed in order to create a self-signed certificate and private key file using the Microsoft Windows 7 SDK:
- Latest version of Microsoft .NET Framework 4
- Microsoft Windows SDK for Windows 7 and .NET Framework 4
- Latest version of OpenSSL for Windows
Creating the self-signed certificate using makecert.exe
- Navigate to the folder containing
makecert.exe; by default, it is located under:C:\Program Files\Microsoft SDKs\Windows\v7.1\Bin - Enter the following command:
makecert -r -pe -n "CN=<certificate name>" -b <begin date mm/dd/yyyy> -e <end date mm/dd/yyyy> -ss my -len 4096
Loading the certificate using Microsoft Management Console
- Hit WIN+R, type "mmc" in the field (no quotes), then press enter; this should bring up the Microsoft Management Console
- Click the "File" dropdown, then click "Add/Remove Snap-in"
- Click "Certificates" on the left table, then click the "Add" button
- Click the "My user account" radio button, then click "Next"
- Under "Console Root", expand the "Certificates - Current User" list
- Expand the "Personal" folder, then click "Certificates"
- Right-click the certificate with the name you just created, hover over "All Tasks", then click "Export"
Exporting the .CER certificate
- In the Certificate Export Wizard, click "Next"
- Click "No, do not export the private key", then click "Next"
- Click "Base-64 encoded X.509 (.CER)", then click "Next"
- Choose a name for the file, then click "Browse" to save the file in a location of your choosing
- Click "Next", then click "Finish"; a popup should display that the certificate was successfully exported
Exporting the .PFX password-protected private key certificate
- Still in the Microsoft Management Console, right-click the certificate with the name you just created earlier, hover over "All Tasks", then click "Export"
- In the Certificate Export Wizard, click "Next"
- Click "Yes, export the private key", then click "Next"
- Click "Personal Information Exchange - PKCS #12 (.PFX)", then click "Next"
- Enter a password of your choosing, confirm it, then click "Next"
- Choose a name for the file, then click "Browse" to save the file in a location of your choosing
- Click "Next", then click "Finish"; a popup should display that the certificate was successfully exported
Converting the .PFX file to a .PK8 file
- Navigate to the folder containing OpenSSL
- Enter the following command to convert from .PFX to .PEM:
- openssl pkcs12 -in <your .PFX file> -nocerts -nodes -out <file name>.pem
- When prompted, enter the password used when you exported the PFX file
- Enter the following command to convert from .PEM to .PK8:
- openssl pkcs8 -in <your .PEM file> -topk8 -nocrypt -out <file name>.pk8
Extracting File Information
Extracting X.509 Public Certificate Information
This section assumes you have acquired a Base-64 encoded X.509 public certificate, which is a PEM encoded .CER, .CRT, or .PEM file. If you are in a development environment or did not acquire such a certificate through your certificate authority of choice, you may create a self-signed one using the instructions provided in the Self-Signed Public Certificates for DMS documentation.
Open a Powershell command prompt and enter the following commands:
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$cert.Import("<path to your .CER/.CRT/.PEM file>")
$rawCert = $cert.GetRawCertData()
$base64Cert = [System.Convert]::ToBase64String($rawCert)
$rawCertHash = $cert.GetCertHash()
$base64CertHash = [System.Convert]::ToBase64String($rawCertHash)
$guid = [System.Guid]::NewGuid().ToString()
Write-Host $base64Cert
Take note of the value printed out, as this is your value for Azure Active Directory; note that this is a large character string, and care should be taken to delete any line breaks in between characters
Write-Host $base64CertHash
Take note of the value printed out, as this is your customKeyIdentifier for Azure Active Directory, as well as your Thumbprint for the SharePoint Online integration
Write-Host $guid
Take note of the value printed out, as this is your keyId for Azure Active Directory
Extracting PKCS #8 Private Key Information
This section assumes you have acquired a Base-64 encoded PKCS #8 private key, which is a .PK8 file. Due to its sensitive content, if this file has been supplied for the sole purpose of authorizing TeamConnect to communicate with SharePoint Online, it is strongly recommended after setting up your integration(s) that you either move this file to a secure location or remove it from your system entirely. Once these contents have been supplied to TeamConnect through the DMS Connector page, they will be obfuscated in the user interface upon entry and encrypted within the database for secure storage. If you are in a development environment or did not acquire such a file through your certificate authority of choice, you may create one using the instructions provided in the Self-Signed Public Certificates for DMS documentation.
Extracting .PK8 file information
- Open the file In a text editor, such as Notepad
- In between the lines that say "-----BEGIN PRIVATE KEY-----" and "-----END PRIVATE KEY-----", copy the contents.
Take note of the value printed out, as this is your Key for the SharePoint Online integration; note that this is a large character string, and care should be taken to delete any line breaks in between characters
Creating the Application Profile
Setting up the application profile
To create an application profile for TeamConnect to use when communicating with Azure Active Directory and SharePoint Online, see: https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-integrating-applications#adding-an-application
In the process of creating a new application profile, you will be prompted to specify values which should be entered/selected as follows:
- For Name, enter any name of your choice to identify the application
- Under Application type, ensure that the Web app / API option is selected
- Under Sign-on URL, enter any valid URL. Note: This URL is required to finish setting up the profile but will not be used for any reason by TeamConnect.
Retrieving the Tenant ID
When viewing the list of registered applications present in the tenancy, under Endpoints, observe the field: OAUTH 2.0 TOKEN ENDPOINT; in this field, there will be a URL containing a GUID in the form of: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx.
Take note of the GUID, as this is your TenantID for the SharePoint Online integration.
Retrieving the Client ID
Open the profile of the application you just registered and observe the string under Application ID; take note of the value displayed, as this is your ClientID for the SharePoint Online integration
Adding required permissions to the application profile
To add permissions to the application profile used by TeamConnect, and subsequently, grant its use within your Office 365 tenancy, see: https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-integrating-applications#updating-an-application
Users must ensure that the Grant Permissions button has been clicked for the DMS Connector to work properly.
Editing the application profile's manifest
To supply Azure Active Directory with the credentials required for TeamConnect to securely communicate with it, see: https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-application-manifest
Edit the keyCredentials property of your manifest using the following schema:
"keyCredentials": [
{
"value": "<your value from Extracting X.509 Public Certificate Information>",
"customKeyIdentifier": "<your customKeyIdentifier from Extracting X.509 Public Certificate Information>",
"keyId": "<your keyId from Extracting X.509 Public Certificate Information>",
"type": "AsymmetricX509Cert",
"usage": "Verify"
}
]
Setting up the Integration in TeamConnect
Uploading the .CLASS file and .PROPERTIES file to TeamConnect
Ensure that you have acquired the latest versions of both a SharePointOnlineIntegration.class file and SharePointOnlineIntegration.properties file, which comprise the SharePoint Online integration for TeamConnect.
- In your TeamConnect instance, under the Documents tab, navigate to the Integrations folder, which can be found through: Top Level -> System -> Integrations
- In the Integrations folder, create a new folder
- In this new folder, upload the SharePointOnlineIntegration.class file and the SharePointOnlineIntegration.properties file.
Creating a DMS integration record in the DMS Connector Tool
- Under the Tools icon in the top right of your TC application, select DMS Connector
- For Type, select the option that corresponds with the name of the folder you created earlier
- For Name, enter a name to be used when displaying this record
- If you would like this integration to be your default DMS, check Default
- For Key, enter your Key from the “Extracting
.PK8File Information” section - For URL, enter the address of your SharePointOnline site or subsite, e.g., https://site.sharepoint.com/ or https://site.sharepoint.com/subsite/
- For DocumentLibraryName, enter the name of an existing SharePoint Online Document Library for TeamConnect to use
- For RootFolder, enter the name of an existing SharePoint Online folder located directly under the Document Library
- For TenantID, enter the tenant ID retrieved earlier.
- For ClientID, enter the client ID retrieved earlier.
- For Thumbprint, enter your Thumbprint from the “Extracting
.CERFile Information” section - For CreatedByTitle, enter the column name from the Sharepoint Library to be used for TeamConnect to display the user who created the document
- For ModifiedByTitle, enter the column name from the Sharepoint Library to be used for TeamConnect to display the user who last modified the document
- For ProjectNameTitle, enter the column name from the Sharepoint Library to be used for TeamConnect to display the friendly name of a project record
- Ensure that the column type is "Single line of text" for items 12-14 of this list; see the following link to learn how to create a new column for your document library
- Click Add DMS integration to finish creating the record
Testing the credentials
For the SharePoint Online integration record, clicking the Test DMS icon will verify that all of your security credentials are valid and that your DocumentLibraryName and RootFolder exist.

