Oauth 2 for CMO Mailboxes
CMO mailboxes authentication mechanism has been upgraded from basic authentication to Oauth2. To access emails, the service accounts configured with CMO application currently needs basic authentication. From 2021, in order to connect, those accounts which are using the EWS protocol to connect to 365 require Modern Authentication, i.e. Oauth2.
Mailbox Configuration to Send Email
Following key controls is used to mails
<add key="Mail.Sending.ServerType" value="" />
Available options:
- Smtp (it’s also a default value when value is not empty)
- Microsoft365
SMTP has following Configuration:
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Sending.Smtp.Server |
String |
SMTP server address, may include port (if port is not specified, then CMO selects port based on option specified for SSL). |
Yes |
|
|
Mail.Sending.Smtp.NumberOfMessagesPerSession |
String |
Controls how many messages will be send within the same session. When this limit is exceeded, CMO resets existing connection and initiate new. |
Yes |
3 |
|
Mail.Sending.Smtp.UseAuth |
Boolean |
Controls if CMO connect to SMTP server anonymously or not. |
Yes |
False |
|
Mail.Sending.Smtp.UseSsl |
Boolean |
Controls if SSL (TLS) is used or not. |
|
False |
|
Mail.Sending.Smtp.AuthType |
String |
Controls what authentication type / way is used. Possible values:
|
Yes |
BasicAuth |
Basic Auth configuration:
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Sending.Smtp.Login |
String |
Login used to connect to SMTP server |
Yes |
 |
|
Mail.Sending.Smtp.Password |
String |
Password used to connect to SMTP server |
Yes |
 |
Google OAuth2 Configuration:
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
|
Mail.Sending.Smtp.GoogleOAuth2.CertificatePath |
String |
Path to certificate for the service account. It should be path that can be used as is (without any additional resolving) to access the certificate (for account under website (IIS) is running) |
Yes |
 |
|
|
Mail.Sending.Smtp.GoogleOAuth2.ServiceAccount |
String |
Name of service account |
Yes |
 |
|
| Mail.Sending.Smtp.GoogleOAuth2.GsuiteUser | String | Name of gsuite user to impersonate service account | Yes |  |
|
Microsoft 365 has following Configuration:
CMO supports two different authentication approaches for Microsoft 365. First one uses special service account user and requires admin consent (call it confidential application approach), second one allows to use regular (work / school) Microsoft 365 account and doesn’t require admin consent (call it public application approach).
Following setting controls what approach is used: Mail.Sending.Microsoft365.IntegrationType. It’s mandatory, has no default value. Possible values are Confidential and Public.
To use Public authentication flow a token must be configured. See ‘Configuring token for Microsoft 365 public application’ for the details.
Confidential Application Configuration:
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Sending.Microsoft365.ConfidentialApp.ClientId |
String |
The client ID (a string representing a GUID) |
Yes |
|
|
Mail.Sending.Microsoft365.ConfidentialApp.TenantId |
String |
The tenant ID |
Yes |
|
|
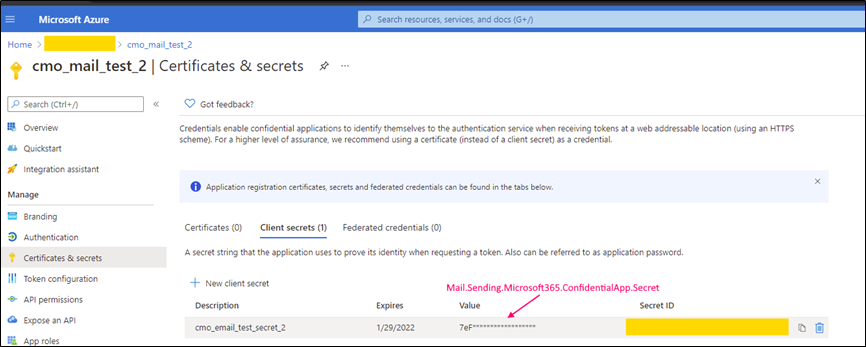
Mail.Sending.Microsoft365.ConfidentialApp.Secret |
String |
The application secret (client secret string) |
Yes |
|
|
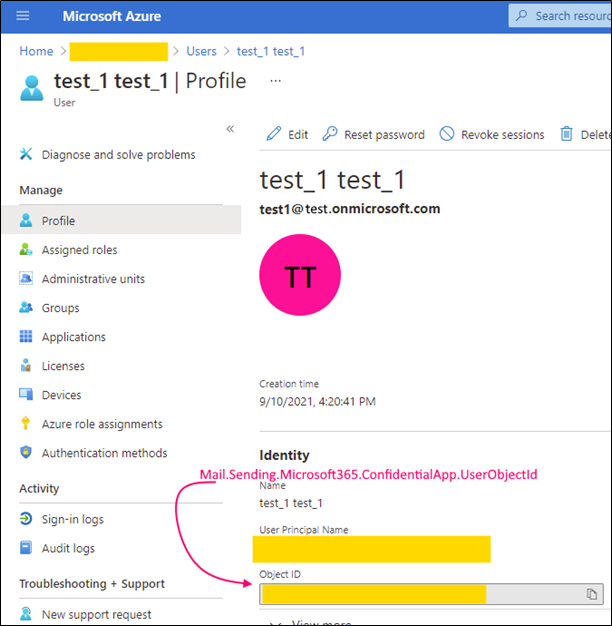
Mail.Sending.Microsoft365.ConfidentialApp.UserObjectId |
String |
Account Id (a string representing a GUID) of a user used to send / receive messages. |
Yes |
|
Following Graph API scopes are required (Application permissions, Admin consent must be provided):
- Mail.Read
- Mail.ReadWrite
- Mail.Send
Public Application Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Sending.Microsoft365.PublicApp.ClientId |
String |
The client ID (a string representing a GUID) |
Yes |
|
|
Mail.Sending.Microsoft365.PublicApp.TenantId |
String |
The tenant ID |
Yes |
|
|
Mail.Sending.Microsoft365.PublicApp.RedirectUri |
String |
The identity provider URL (named the instance) and the sign-in audience |
Yes |
|
|
Mail.Sending.Microsoft365.PublicApp.AccountName |
String |
User name of the MS 365 user account that can be by Web App to communicate with Graph API to send / receive messages. |
Yes |
|
Following Graph API scopes are required (Delegated permissions):
- Mail.Read
- Mail.ReadWrite
- Mail.Send
- offline_access
To use Public authentication flow a token must be configured. See ‘Configuring token for Microsoft 365 public application’ for the details.
Mailbox Configuration to Receive Email
The key Mail.Receiving.ServerType controls what way is used to receive messages. Possible values are:
- IMAP
- POP3
- MAPI
- Microsoft365
Note: Nothing has been changed for the MAPI (it works in the same way as before).
IMAP Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Imap.Server |
String |
IMAP server address, may include port (if port is not specified, then CMO selects port based on option specified for SSL). |
Yes |
|
|
Mail.Receiving.Imap.UseSSL |
Boolean |
Controls if SSL (TLS) is used or not. |
Yes |
False |
|
Mail.Receiving.Imap.AuthType |
String |
Controls what authentication type / way is used. Possible values:
|
Yes |
BasicAuth |
Basic Auth Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Imap.Login |
String |
Login used to connect to SMTP server |
Yes |
|
|
Mail.Receiving.Imap.Password |
String |
Password used to connect to SMTP server |
Yes |
|
Google OAuth2 Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Imap.GoogleOAuth2.CertificatePath |
String |
Path to certificate for the service account. It should be path that can be used as is (without any additional resolving) to access the certificate (for account under website (IIS) is running) |
Yes |
|
|
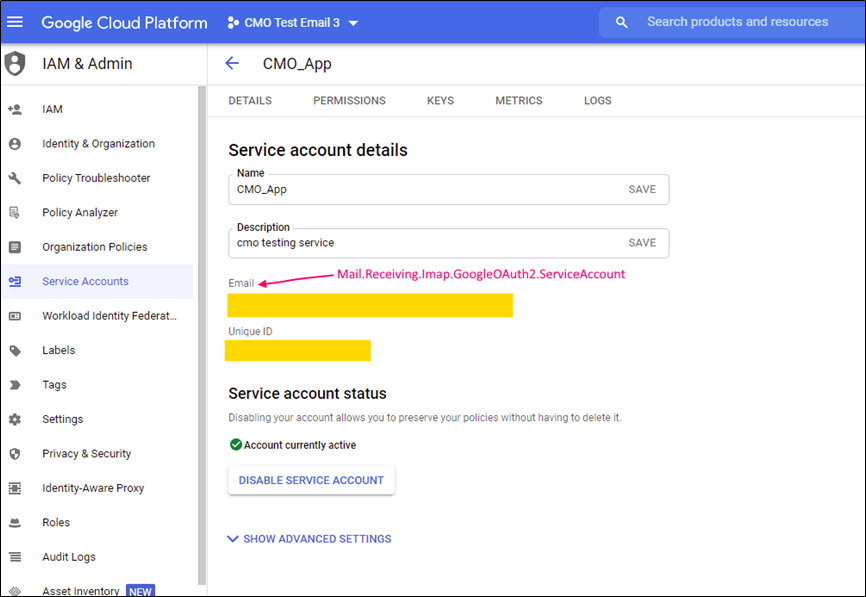
Mail.Receiving.Imap.GoogleOAuth2.ServiceAccount |
String |
Name of service account |
Yes |
|
|
Mail.Receiving.Imap.GoogleOAuth2.GsuiteUser |
String |
Name of gsuite user to impersonate service account |
Yes |
|
POP3 Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Pop3.Server |
String |
Pop server address, may include port (if port is not specified, then CMO selects port based on option specified for SSL). |
Yes |
|
|
Mail.Receiving.Pop3.UseSSL |
Boolean |
Controls if SSL (TLS) is used or not. |
Yes |
False |
|
Mail.Receiving.Pop3.AuthType |
String |
Controls what authentication type / way is used. Possible values:
|
Yes |
BasicAuth |
Basic Auth Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Pop3.Login |
String |
Login used to connect to SMTP server |
Yes |
 |
|
Mail.Receiving.Pop3.Password |
String |
Password used to connect to SMTP server |
Yes |
 |
GoogleOAuth2 Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Pop3.GoogleOAuth2.CertificatePath |
String |
Path to certificate for the service account. It should be path that can be used as is (without any additional resolving) to access the certificate (for account under website (IIS) is running) |
Yes |
 |
|
Mail.Receiving.Pop3.GoogleOAuth2.ServiceAccount |
String |
Name of service account |
Yes |
 |
|
Mail.Receiving.Pop3.GoogleOAuth2.GsuiteUser |
String |
Name of gsuite user to impersonate service account |
Yes |
 |
Microsoft 365 Configuration
Receiving message also supports two different approaches for authentication: Public and Confidential (it is exactly the same as for sending). The key Mail.Receiving.Microsoft365.IntegrationType controls what approach is used. Possible values are Confidential, Public. It’s mandatory, has no default value.
Confidential Application Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Microsoft365.ConfidentialApp.ClientId |
String |
The client ID (a string representing a GUID) |
Yes |
 |
|
Mail.Receiving.Microsoft365.ConfidentialApp.TenantId |
String |
The tenant ID |
Yes |
 |
|
Mail.Receiving.Microsoft365.ConfidentialApp.Secret |
String |
The application secret (client secret string) |
Yes |
 |
|
Mail.Receiving.Microsoft365.ConfidentialApp.UserObjectId |
String |
Account Id (a string representing a GUID) of a user used to send / receive messages. |
Yes |
 |
Following Graph API scopes are required (Application permissions, Admin consent must be provided): Mail.Read, Mail.ReadWrite, Mail.Send.
Public Application Configuration
|
Key |
Type |
Remark |
Mandatory |
Default value |
|
Mail.Receiving.Microsoft365.PublicApp.ClientId |
String |
The client ID (a string representing a GUID) |
Yes |
 |
|
Mail.Receiving.Microsoft365.PublicApp.TenantId |
String |
The tenant ID |
Yes |
 |
|
Mail.Receiving.Microsoft365.PublicApp.RedirectUri |
String |
The identity provider URL (named the instance) and the sign-in audience |
Yes |
 |
|
Mail.Receiving.Microsoft365.PublicApp.AccountName |
String |
User name of the MS 365 user account that can be by Web App to communicate with Graph API to send / receive messages. |
Yes |
 |
Following Graph API scopes are required (Delegated permissions): Mail.Read, Mail.ReadWrite, Mail.Send, offline_access.
To use Public authentication flow a token must be configured. See ‘Configuring token for Microsoft 365 public application’ for the details.
Document Import and New Action Mailboxes
CMO has ability to use different mailboxes for document import and new action. They allow to override some parameters (but not all). Other parameters are inherited from Mail.Receiving. Configuration keys for these mailboxes have exactly the same meaning, type, possible values, etc., therefore only names of those keys are provided:
- Mail.NewAction.EmailClient.AuthType
- Mail.NewAction.EmailClient.GoogleOAuth2.CertificatePath
- Mail.NewAction.EmailClient.GoogleOAuth2.ServiceAccount
- Mail.NewAction.EmailClient.GoogleOAuth2.GsuiteUser
- Mail.NewAction.EmailClient.Server
- Mail.NewAction.EmailClient.Login
- Mail.NewAction.EmailClient.Password
- Mail.NewAction.EmailClient.Microsoft365.IntegrationType
- Mail.NewAction.EmailClient.Microsoft365.PublicApp.ClientId
- Mail.NewAction.EmailClient.Microsoft365.PublicApp.TenantId
- Mail.NewAction.EmailClient.Microsoft365.PublicApp.RedirectUri
- Mail.NewAction.EmailClient.Microsoft365.PublicApp.AccountName
- Mail.NewAction.EmailClient.Microsoft365.ConfidentialApp.ClientId
- Mail.NewAction.EmailClient.Microsoft365.ConfidentialApp.TenantId
- Mail.NewAction.EmailClient.Microsoft365.ConfidentialApp.Secret
- Mail.NewAction.EmailClient.Microsoft365.ConfidentialApp.UserObjectId
- Mail.DocumentImport.EmailClient.AuthType
- Mail.DocumentImport.EmailClient.GoogleOAuth2.CertificatePath
- Mail.DocumentImport.EmailClient.GoogleOAuth2.ServiceAccount
- Mail.DocumentImport.EmailClient.GoogleOAuth2.GsuiteUser
- Mail.DocumentImport.EmailClient.Server
- Mail.DocumentImport.EmailClient.Login
- Mail.DocumentImport.EmailClient.Password
- Mail.DocumentImport.EmailClient.Microsoft365.IntegrationType
- Mail.DocumentImport.EmailClient.Microsoft365.PublicApp.ClientId
- Mail.DocumentImport.EmailClient.Microsoft365.PublicApp.TenantId
- Mail.DocumentImport.EmailClient.Microsoft365.PublicApp.RedirectUri
- Mail.DocumentImport.EmailClient.Microsoft365.PublicApp.AccountName
- Mail.DocumentImport.EmailClient.Microsoft365.ConfidentialApp.ClientId
- Mail.DocumentImport.EmailClient.Microsoft365.ConfidentialApp.TenantId
- Mail.DocumentImport.EmailClient.Microsoft365.ConfidentialApp.Secret
- Mail.DocumentImport.EmailClient.Microsoft365.ConfidentialApp.UserObjectId
Note: The same account can be used to send / receive emails when Microsoft 365 is used.
Configuring Token for Microsoft 365 Public Application
To configure token (Public Application auth flow) CMO.Microsoft365TokenHelper tool should be used. The tool is available in package folder of website.
The tool has following configuration:
- <add key="ClientId" value=""/>
- <add key="TenantId" value=""/>
- <add key="RedirectUri" value=""/>
- <add key="CacheFileName" value=""/>
- <add key="CacheDirectory" value=""/>
ClientId, TenantId, RedirectUri are the same as for Web App configuration. CacheFileName (default value is cmo_msal_cache.dat) controls name of cache file which will be created and used to store serialized OAuth 2.0 tokens. CacheDirectory controls directory where that file will be created. To serialize token use following steps:
- Specify parameters in the configuration file.
- Run the tool.
- Enter ‘Y' to add token or ‘N’ (anything except 'Y’) to quit.
- In the opened dialog box enter credentials for a valid MS 365 account.
- Review and accept all requested permissions.
- Repeat steps 3-5 for all required mailboxes.
Once cache file is generated go to Web app and put the file to directory (or generate the file to that directory using CacheDirectory configuration option) available for Web app instance. In the web config set following settings (based on the generated file name and its location):
- <add key="MSAL.Cache.Folder" value="" />
- <add key="MSAL.Cache.FileName" value="" />
Note: The tool uses Local Machine protection scope, hence the tool must be run on web server. In case when a few web application instances points to the same db need to repeat that procedure for every server or configure to use the scheduler for specific web server (web application instance).
To verify that CMO is able to authenticate request to Graph API (to send and receive messages) use the following dialog (available under SA account):
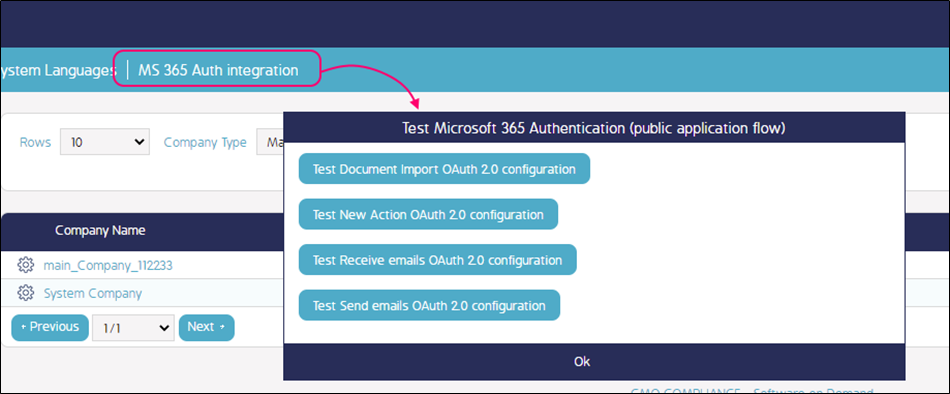
Azure Configuration
Following parameters should be configured and specified in the web.config (for corresponding keys) in order to use 'Confidential application auth flow (for example to send emails).
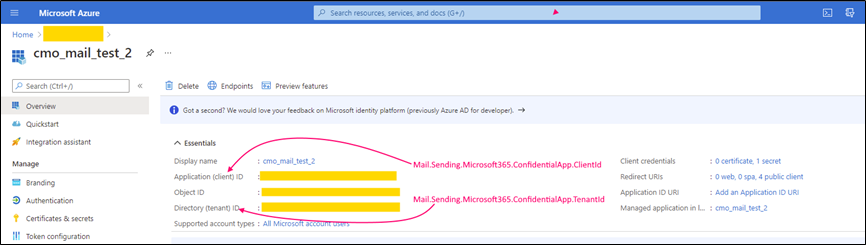
Configuration to receive emails (or create Action / Document via email) is the same, just use corresponding prefix instead of Mail.Sending, e.g. Mail.Receiving.Microsoft365.ConfidentialApp.ClientId instead of Mail.Sending.Microsoft365.ConfidentialApp.ClientId.
Following parameters should be configured and specified in the web.config (for corresponding keys) in order to use 'Public application auth flow (for example to send emails).
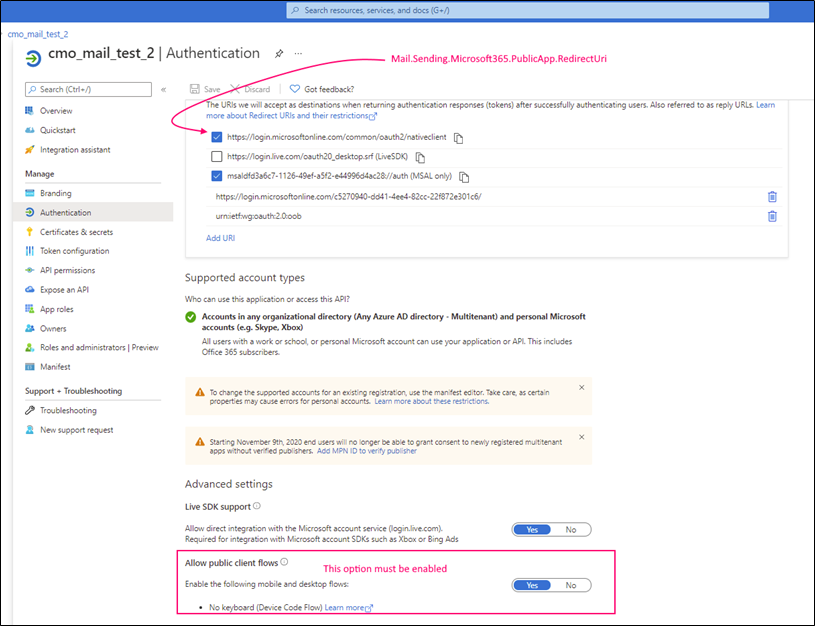
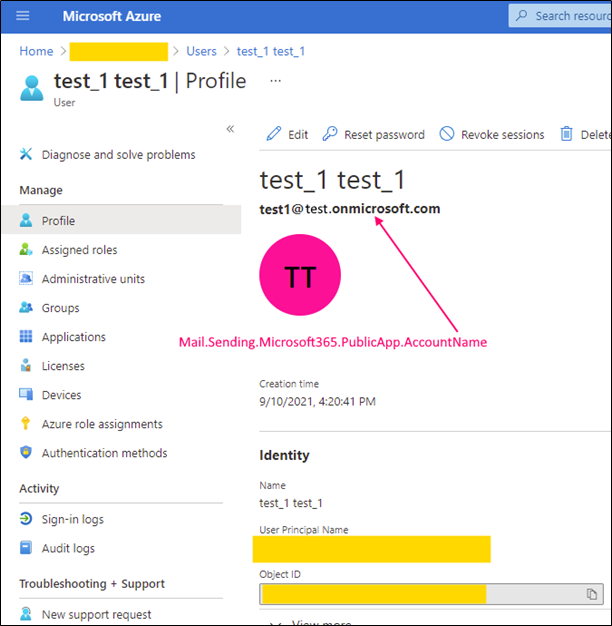
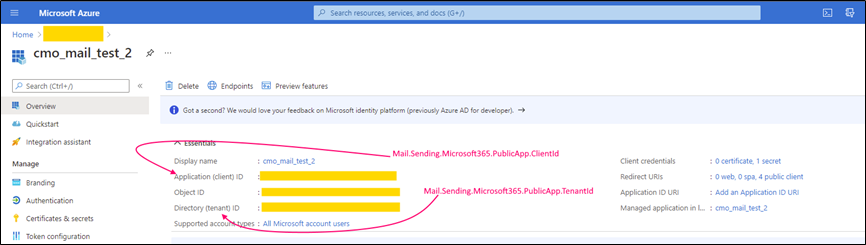
Configuration to receive emails (or create Action / Document via email) is the same, just use corresponding prefix instead of Mail.Sending, e.g. Mail.Receiving.Microsoft365.PublicApp.ClientId instead of Mail.Sending.Microsoft365.PublicApp.ClientId.
Google Mail Configuration
Mail.Google.Com (https://mail.google.com/) scope is required (that allows to read, compose, send, and permanently delete all your email from Gmail). It can be configured here:
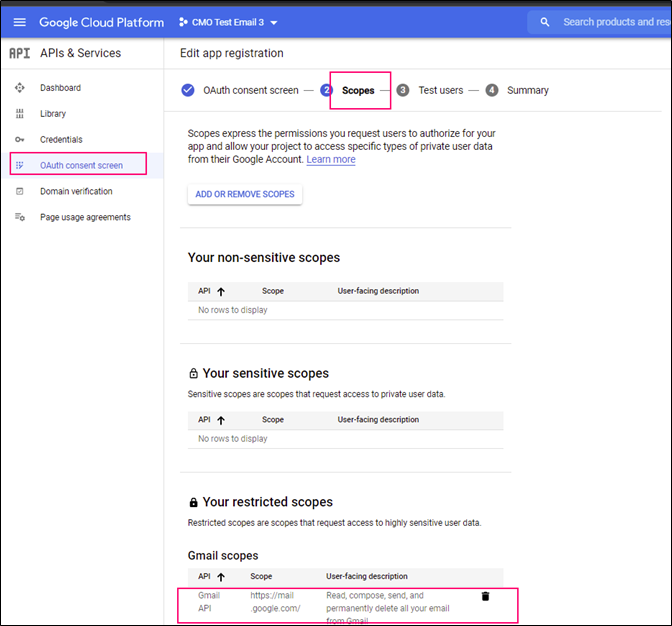
Service account can be configured here:
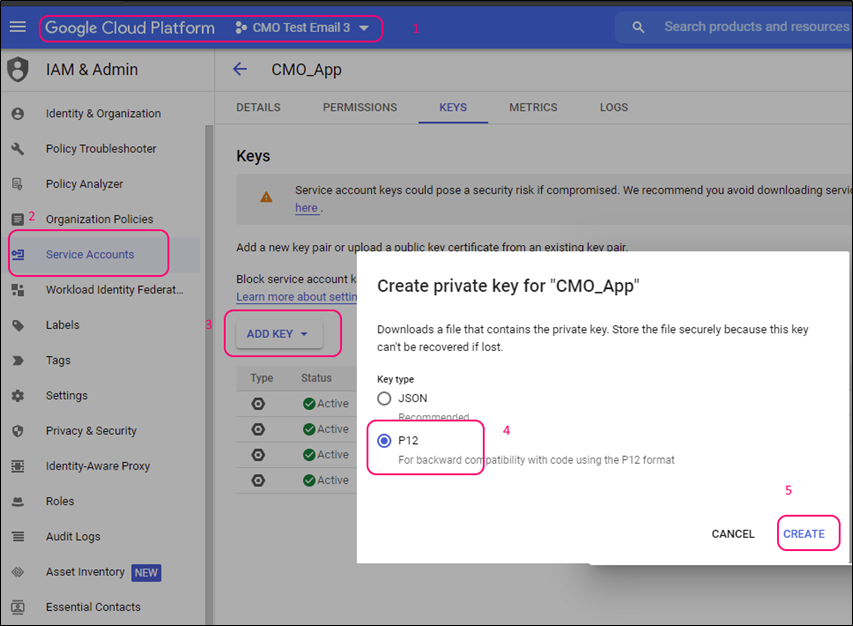
Project can be created using this screen: